NVIDIA’s Nemotron 3: Pioneering Open, Efficient Models for the Agentic AI Era
NVIDIA has officially launched the Nemotron 3 family of open models, marking a major advancement in transparent, high-performance AI built for the agentic era. First announced in late 2025, this release includes model weights, extensive training datasets, and full reinforcement learning recipes—empowering developers to build specialized multi-agent systems with unprecedented visibility. Unlike closed-source alternatives, Nemotron…

Linux kernel 7.0 supports net namespace in AF_VSOCK.
The Linux kernel version 7.0 now supports network namespaces in AF_VSOCK. This fixes issues in how virtual sockets work in isolated environments like containers. It’s exciting for anyone working with virtualization! What is AF_VSOCK? Let’s start simple. In normal networking, programs use sockets to talk over the internet or local networks. These use address families…

CopilotKit: The Open-Source Framework Revolutionizing In-App AI Copilots
In 2026, AI agents are no longer just chatbots or external tools—they’re becoming deeply integrated parts of applications themselves. Developers increasingly want to build “agentic” experiences where AI can understand app context, control UI elements, execute actions, and collaborate with users in real time. Enter CopilotKit, an open-source framework that’s rapidly gaining traction for making…

Exploring Kine: The Etcd Shim Revolutionizing Kubernetes Storage
In the world of container orchestration, Kubernetes is the de facto standard. However, its core component—the etcd key-value store—can be a heavyweight dependency for edge environments or small clusters. Enter K3s, Rancher’s minimalist distribution, and its secret weapon: Kine. What is Kine? Kine (pronounced “kine” like “bovine”) is an open-source etcd shim. It acts as…
Bring AI Vision to the Edge: Weaviate Releases CLIP Inference Support for NVIDIA Jetson
The frontier of “Edge AI” just moved a significant step forward. In a recent announcement on X (formerly Twitter), vector database pioneer Weaviate revealed that its Multi2Vec CLIP inference container (v1.5.0) now officially supports NVIDIA Jetson devices. This update bridges the gap between powerful multimodal AI models and energy-efficient edge hardware, allowing developers to run…

Capturing Network Traffic Over Cilium VTEP Tunnels with eBPF: A Practical Guide
In modern Kubernetes environments, connecting external systems—like virtual machines, legacy appliances, or third-party load balancers—to pods often requires overlay tunneling. Cilium’s VTEP (VXLAN Tunnel Endpoint) integration makes this seamless by allowing direct VXLAN communication between Cilium-managed pods and external VTEP devices. But how do you actually observe and debug the traffic flowing through these tunnels…

From Prompting to Autonomy: 10 GitHub Repos to Master AI Agents
The transition from simple LLM chatting to building autonomous AI agents is the biggest shift in software engineering today. While the field moves fast, these 10 repositories represent the “Gold Standard” of learning resources, offering everything from foundational math to production-grade deployment patterns. Foundations and Frameworks 1. Hands-On Large Language Models The Deep Dive: This…

MadeWithML: Mastering the First Principles of Production AI
In the high-stakes world of machine learning, there is a notorious “valley of death” between a model that works on a data scientist’s laptop and one that actually delivers value in production. Most online courses focus on the former—teaching you how to optimize a loss function or pick the right architecture. But as any veteran…
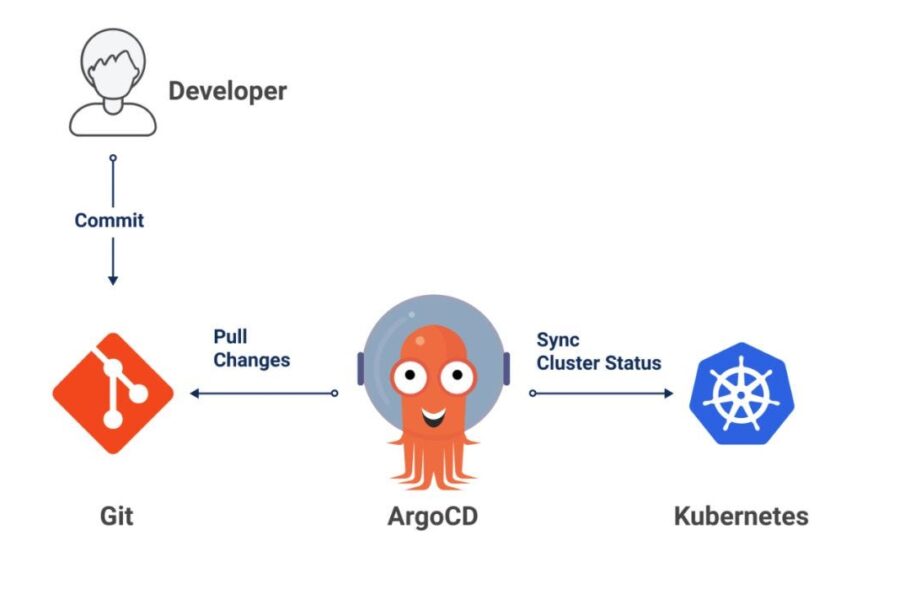
Mastering Argo CD Diffing: Why Changes Go Unnoticed and How to Fix It
Argo CD is a cornerstone of GitOps for Kubernetes, continuously reconciling the desired state defined in Git (or Helm/OCI sources) with the live cluster state. At the heart of this reconciliation lies diffing—the process of comparing manifests to detect drifts, mutations, or manual changes. When diffing fails to spot differences, applications can appear “OutOfSync” unexpectedly…

AWS Introduces Strands Agents: A Model-Driven Revolution in Building Robust AI Agents
In the rapidly evolving world of AI agents, developers often face a familiar frustration: what begins as a simple goal quickly spirals into complex prompt engineering, custom routing logic, intricate error handling, tool orchestration, and brittle fallback mechanisms. One unexpected user input can cause the entire system to collapse. AWS is changing this paradigm with…

Anthropic Donates Model Context Protocol and Launches Agentic AI Foundation: A Step Toward Open AI Standards
In a significant move for the AI ecosystem, Anthropic — the company behind the Claude family of large language models — has announced the donation of its Model Context Protocol (MCP) to the public domain and the establishment of the Agentic AI Foundation. This development signals a push toward greater interoperability, standardization, and collaborative progress…

From Vibe-Coding Chaos to Spec-Driven Precision: Why 2025’s Hottest AI Engineering Practice Is Redefining Reliable Code
As AI-assisted coding continues to reshape software development in 2025 and beyond, a clear divide has emerged between casual, improvisational approaches and more disciplined methodologies. The rise of “vibe-coding” — a term popularized by AI pioneer Andrej Karpathy in early 2025 — allowed developers (and even non-coders) to describe ideas in natural language, letting large…
