Date and Time : September 17 |...
Read MoreFrom Prompting to Autonomy: 10 GitHub Repos to Master AI Agents
The transition from simple LLM chatting ...
AWS Introduces Strands Agents: A Model-Driven Revolution in Building Robust AI Agents
In the rapidly evolving world of AI ...
Anthropic Donates Model Context Protocol and Launches Agentic AI Foundation: A Step Toward Open AI Standards
In a significant move for the AI ...
Mastering Agent Development: How LangSmith Simplifies Building Reliable AI Agents
In the rapidly evolving world of AI, ...
Centralizing Helm: Why Ingress Failed and HTTPProxy Won
As organizations grow, so does the ...
Level Up Your GPU Game: Mastering Advanced CUDA Features in 2026
NVIDIA’s CUDA platform continues ...
Beyond Tool Chaining: Why Code Execution is the Future of AI Agents
In the year since the Model Context ...
Mastering Kubernetes Informers: Lessons from the Trenches to Avoid Costly Mistakes
In the world of Kubernetes, where ...
Avoid Breaking Your Cluster: How Kube No Trouble (kubent) Helps Detect Deprecated Kubernetes APIs
As Kubernetes continues its rapid ...
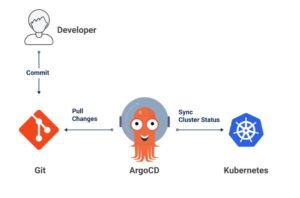
KubeDiagrams: Automatically Generate Stunning Kubernetes Architecture Diagrams from Code and Clusters
In the fast-paced world of Kubernetes, ...