
From Chaos to Continuous Delivery: The DevOps Automation Journey
In a world where technology evolves at lightning speed, the ability to innovate quickly without compromising on quality has become essential for businesses of all sizes. This is where DevOps and automation step in—working together to transform how software is built, tested, deployed, and maintained. By aligning development and operations teams, and automating repetitive processes,…
Redefining Secure Development: A Shift Left Strategy for Modern Teams
In the era of cloud-native applications and rapid release cycles, software teams are under increasing pressure to deliver faster without compromising quality or security. As DevOps continues to drive innovation and streamline workflows, the need for secure-by-design practices is more critical than ever. This is where the “Shift Left” strategy becomes a game-changer—especially when developers…

Join Today’s Grafana Webinar: Master Incident Response and SLOs in Real Time!
Date & Time : APR 30 10:00 CET,08:00 UTC In today’s fast-paced digital landscape, ensuring system reliability and swift incident response is paramount. Grafana’s Incident Response and Management (IRM) suite, combined with Service Level Objectives (SLOs), offers a comprehensive solution to streamline these processes. What is Grafana IRM? Grafana IRM is an integrated solution within…

Boosting IT Support Efficiency with Virtual Assistants in ITSM
In an increasingly digital-first world, IT teams are under pressure to resolve user issues quickly, efficiently, and at scale. As organizations grow and diversify, so does the complexity of managing their IT support landscape. To meet these challenges, Artificial Intelligence (AI) is playing a transformative role in IT Service Management (ITSM)—especially through virtual assistants and…

OpenSearchCon India 2025: Where Innovation Meets Open Source
OpenSearchCon India, hosted by the Linux Foundation, is now accepting registrations for its 2025 edition! Whether you’re a developer, data enthusiast, DevOps engineer, or open-source advocate, this conference is your gateway to the vibrant world of search, analytics, and observability powered by OpenSearch. Event Highlights: Join the Innovation at OpenSearchCon India 2025: Where Open Source…

From Chaos to Control: Why DevOps Teams Love Containers + Kubernetes
A New Era of Software Scalability In today’s rapidly evolving tech landscape, the ability to scale seamlessly can make or break a digital product. From startups experimenting with their first MVP to tech giants serving millions of users globally, scalability is non-negotiable. As applications grow more complex and user demands fluctuate wildly, traditional infrastructure methods…
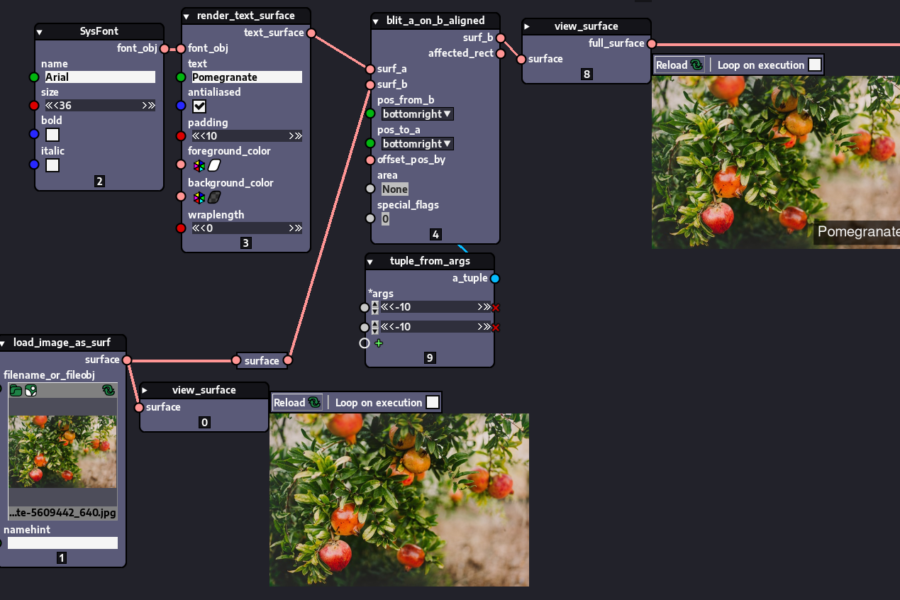
Build, Visualize, and Export Python Code Visually with Nodezator
In the ever-expanding world of Python development, a unique tool is making waves—Nodezator, a visual node-based editor that turns Python functions into interactive building blocks. Whether you’re a developer looking to prototype faster or someone eager to craft low-code/no-code workflows, Nodezator gives Python a new dimension—literally. Let’s dive into what makes this application a game-changer….

AI Agents at Work: A Game-Changer for Workflow Optimization
In recent years, artificial intelligence has shifted from a buzzword to a business imperative. Among the most exciting developments in this space is the rise of AI agents—autonomous, intelligent programs that can reason, learn, and act independently. These agents are not just digital tools; they are becoming active collaborators, reshaping how work gets done and…
