
IaC in 2025: What You Need to Know
Exclusive Webinar: Experts Decode the Biggest IaC Challenges 📅 Date: June 17, 2025🕘 Time: 09:15 PM🎙️ Speakers: Ido Neeman (CEO, Firefly) & Chris Pirillo (Host, The New Stack)🔗 Register Now Cloud chaos is real. If your team is juggling multiple clouds and Infrastructure as Code tools and still struggling to stay ahead, you’re not alone….

Argo CD 3.0 Release Candidate: A Small but Mighty Leap Forward
Argo CD, the popular GitOps continuous delivery tool for Kubernetes, has announced a major leap forward with the release candidate of Argo CD 3.0. This marks the first significant version upgrade since 2021 and signals a more mature, streamlined future for the tool. Designed to enhance security, performance, and usability, version 3.0 incorporates improved default…

5 Beginner-Friendly Resources to Finally Understand AI Agents
The world of AI agents can feel like a maze at first—so many terms, frameworks, and buzzwords. But after digging deep, I found five beginner-friendly resources that make it impossible not to understand what AI agents are and how to build them. Whether you’re just starting out or trying to make sense of all the…

From KubeLB to Cloud Native Zurich: Kubermatic’s Vision in Action
The cloud native landscape is evolving quickly, and staying engaged with the right events is key to keeping up with new technologies, best practices, and expert insights. Kubermatic, a recognized name in Kubernetes automation, has a few upcoming events worth noting for anyone working with or exploring cloud native infrastructure. KubeLB Webinar: Simplifying Multi-Cloud Traffic…
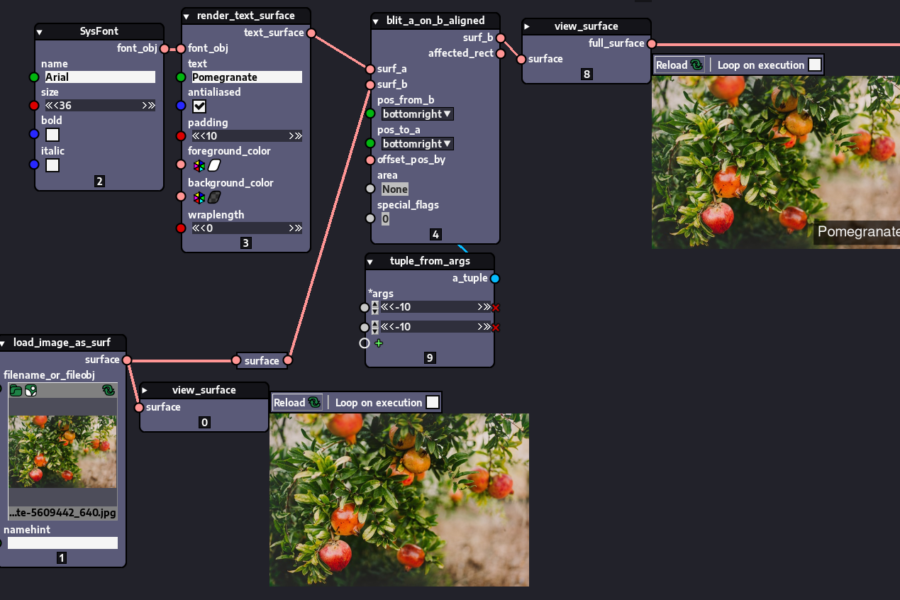
Build, Visualize, and Export Python Code Visually with Nodezator
In the ever-expanding world of Python development, a unique tool is making waves—Nodezator, a visual node-based editor that turns Python functions into interactive building blocks. Whether you’re a developer looking to prototype faster or someone eager to craft low-code/no-code workflows, Nodezator gives Python a new dimension—literally. Let’s dive into what makes this application a game-changer….

From Complexity to Clarity: How KRO is Transforming Kubernetes Management
In the latest episode of the Kubernetes Podcast from Google, hosts welcomed Jesse Butler (Principal Product Manager at AWS) and Nic Slattery (Product Manager at Google) to discuss an exciting new open-source project — the Kubernetes Resource Orchestrator (KRO). Launched through an extraordinary collaboration between Google, AWS, and Microsoft, KRO is designed to make Kubernetes…

The Rise of Kro: Simplified, Vendor-Neutral Kubernetes Orchestration
In a powerful and rare collaboration, tech giants Google, Amazon, and Microsoft have come together to introduce Kro — the Kubernetes Resource Orchestrator — a groundbreaking, open-source tool aimed at streamlining custom resource orchestration within Kubernetes environments. Announced at KubeCon + CloudNativeCon Europe, Kro addresses one of the most pressing needs in the cloud-native ecosystem:…

Accelerate Your CI/CD Journey with Codefresh GitOps Cloud’s Powerful Features
In the world of modern software development, DevOps teams are constantly looking for efficient and scalable solutions to streamline their deployment pipelines. With the increasing complexity of managing multiple environments and clusters, ensuring seamless promotions of applications across those environments can become a daunting task. Enter Codefresh GitOps Cloud — an innovative platform designed to…

Command Your Cloud: Ultimate Project Management with ZOCLI on 01Cloud
Introduction Managing projects efficiently is crucial for developers and organizations. 01Cloud offers a powerful command-line interface, zocli, which enables seamless project management without navigating complex UI settings. This blog will guide you through the essential project commands in zocli, categorized into: Let’s dive into how these commands can optimize your workflow. 1. Basic Commands: Quick…

Authenticating with ZOCli: Fast, Secure, Reliable Access
Overview Authentication is a crucial aspect of securely accessing and managing cloud services. In the 01Cloud ecosystem, authentication through the Command Line Interface (CLI) ensures that only authorized users can perform tasks. The auth command facilitates the authentication process, allowing users to seamlessly log in and manage their sessions within 01Cloud. This command supports various…
