
From DevOps to DevSecOps: The Role of Automation in Modern Security
As the demand for rapid software delivery continues to rise, organizations are increasingly adopting DevOps practices to keep up with innovation cycles. However, speed without security can become a major liability. Traditional security approaches often lag behind modern development cycles, introducing bottlenecks and leaving vulnerabilities unaddressed until it’s too late. This is where DevSecOps —…

From Bottlenecks to Breakthroughs: DevOps and Automation in Action
In today’s hyper-competitive digital economy, speed is everything. Businesses are expected to release new features, products, and updates rapidly—without compromising on quality or security. Traditional software development practices, which often involve handoffs between isolated teams, manual processes, and long deployment cycles, simply can’t keep up. This has given rise to the adoption of DevOps and…
Embedding Zero Trust in DevSecOps: A Modern Security Imperative
In the modern digital landscape, the traditional concept of securing an organization’s infrastructure by building a secure perimeter has become outdated. Businesses are increasingly moving to cloud environments, embracing remote work, and deploying applications across distributed systems. This decentralization makes it extremely difficult to rely on conventional perimeter-based security models, which assume that anything inside…

Why Zero Trust is the Cornerstone of Modern DevSecOps
In the dynamic world of software development and IT operations, speed, efficiency, and reliability are paramount. DevOps, as a cultural and technical shift, has already revolutionized how teams build, test, and deploy software. But the true catalyst for DevOps success lies in automation. Automation enables teams to remove manual bottlenecks, minimize errors, and respond rapidly…

Command Your Cloud: Ultimate Project Management with ZOCLI on 01Cloud
Introduction Managing projects efficiently is crucial for developers and organizations. 01Cloud offers a powerful command-line interface, zocli, which enables seamless project management without navigating complex UI settings. This blog will guide you through the essential project commands in zocli, categorized into: Let’s dive into how these commands can optimize your workflow. 1. Basic Commands: Quick…

OpenAI Academy – Your Gateway to the World of Artificial Intelligence
Artificial Intelligence (AI) is revolutionizing the way we live, work, and interact. From powering smart assistants to driving innovation in healthcare, finance, and automation, AI is transforming industries at an incredible pace. However, access to AI education, tools, and resources has historically been limited to a select group of individuals, elite universities, and large tech…
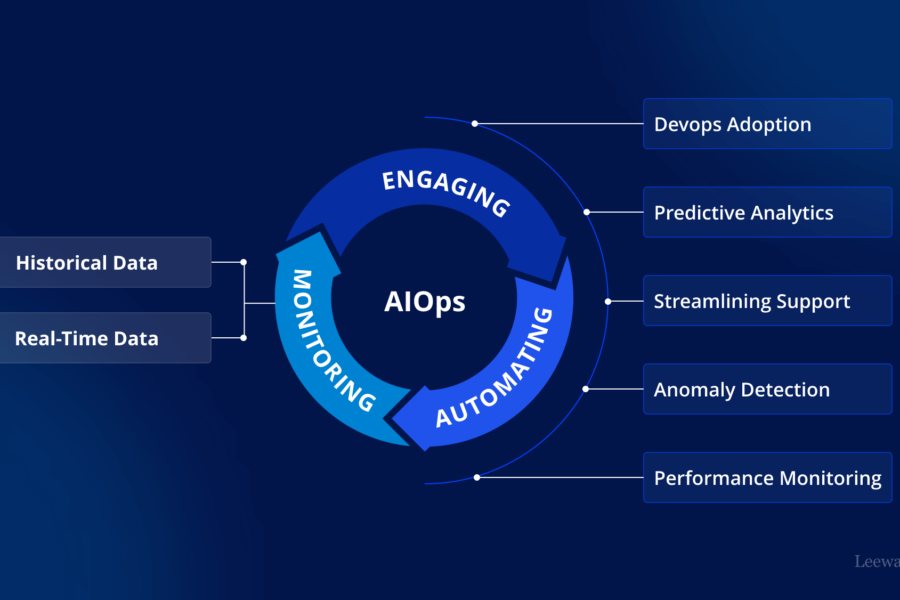
Automating IT: How AIOps Enhances Efficiency
In today’s fast-paced digital landscape, IT operations have become increasingly complex. Organizations are dealing with vast amounts of data generated across networks, cloud environments, and applications. Traditional monitoring and management methods are no longer sufficient to handle this scale and complexity. Artificial Intelligence for IT Operations (AIOps) is revolutionizing IT by introducing automation, predictive analytics,…

Speed, Efficiency, and Innovation: The Automation Advantage in DevOps
In today’s fast-paced digital landscape, businesses must deliver software faster while maintaining high quality and security. Traditional software development processes often struggle with inefficiencies, delays, and human errors. This is where DevOps and automation come into play. By integrating automation into DevOps workflows, organizations can streamline operations, improve collaboration, and accelerate innovation like never before….
