HashiCorp Vault is a secrets management tool provided by HashiCorp. It allows you to securely store and manage sensitive information, such as database credentials, API keys, and other confidential data.
In 01Cloud, HashiCorp Vault can also act as an external secret provider, enabling 01Cloud to access and utilize secrets stored in HashiCorp Vault. This centralizes the management of confidential information and makes it easily accessible from multiple applications, including those operating in a Kubernetes environment.
By utilizing HashiCorp Vault in 01Cloud, you can boost the security and reliability of your applications by separating secrets from the code and reducing the risk of hardcoded secrets in the codebase. Moreover, you can easily update secrets without the need to update the code.
You can explore more about external secret in 01Cloud here.
Steps to create secret in HashiCrop Vault
- let’s create a secret in HashiCorp Vault. Once the vault has been set up within the cluster, log in to Vault using a token.
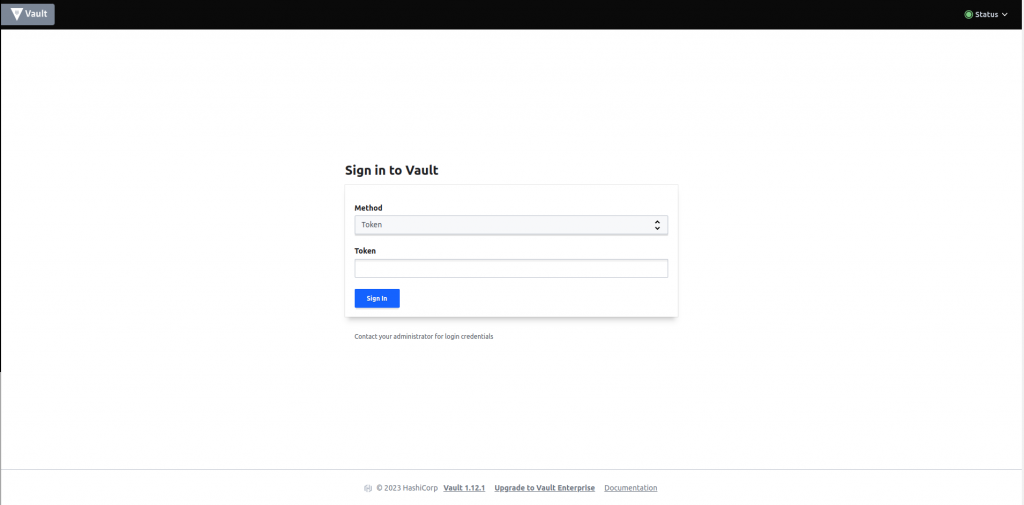
- Upon signing in, it is necessary to activate the new engine. To do this, simply click the “Enable New Engine” button.
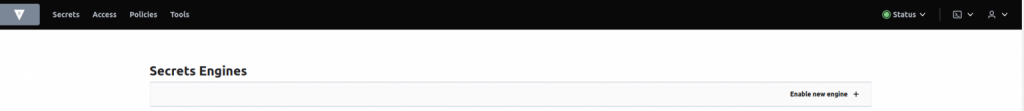
- HashiCorp Vault supports various types of secrets engines. In this instance, let us create a Key-Value (KV) secret.
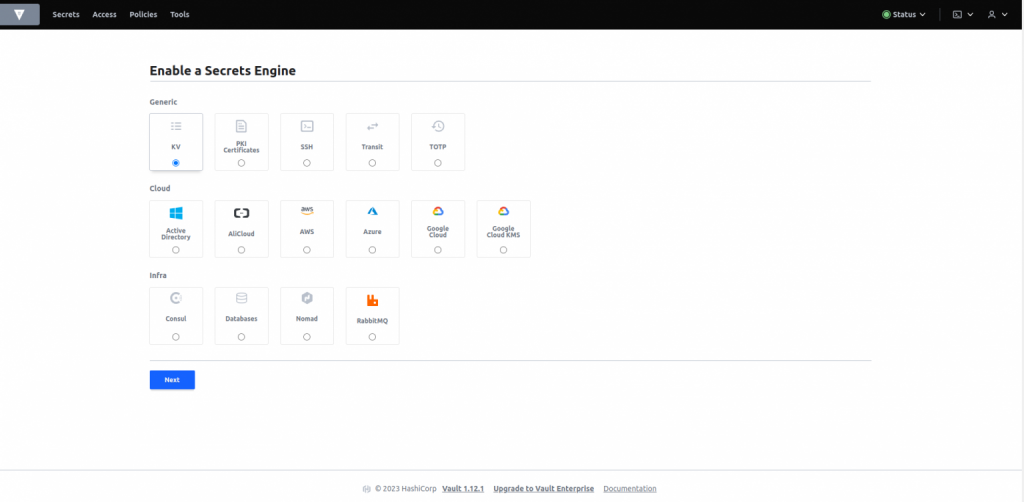
- We have specified the path as “secret”, and after clicking the “Enable Engine” button, a new engine will be created with the “secret” path.
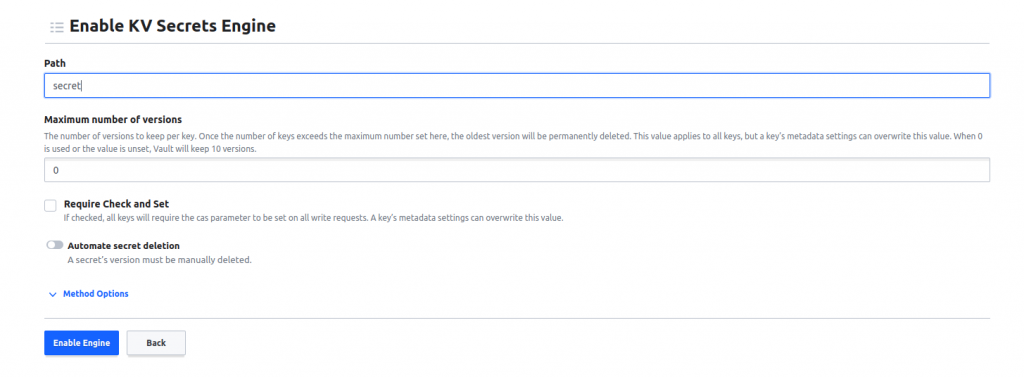
- We have successfully created a new engine with the “secret” path.
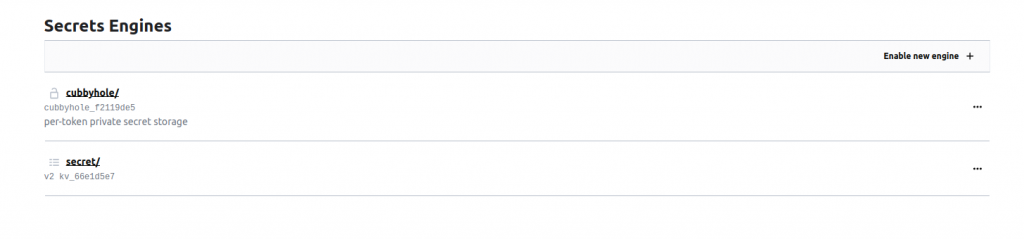
- Within the secret path, there are two tabs available: Secrets and Configuration. To create a new secret, simply navigate to the Secrets tab and click the “Create Secret” button.
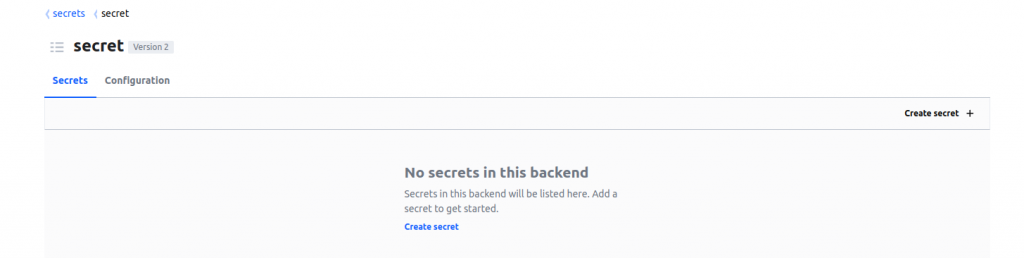
- We have successfully created a secret named ‘cloud01’ and added the necessary data for our use.
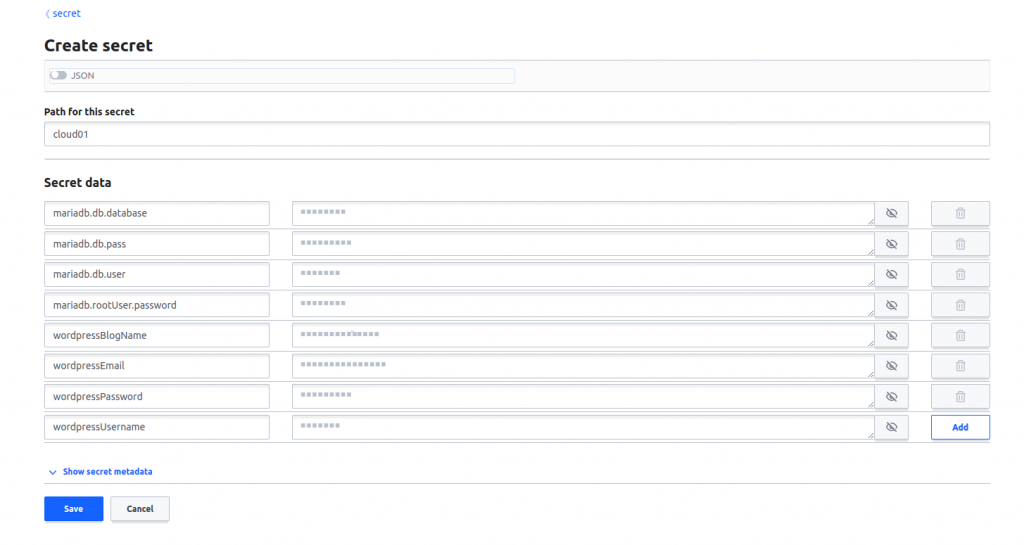
- Upon saving the secret, it should now be visible under the ‘cloud01’ secret.
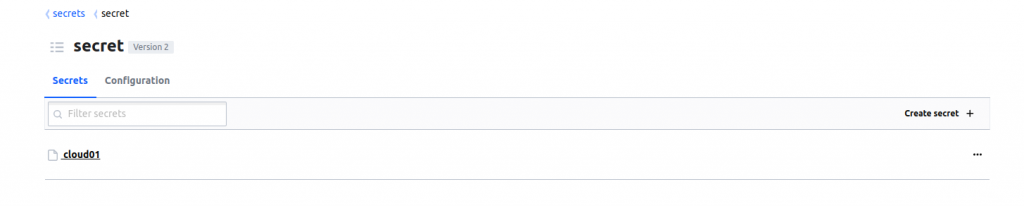
With the creation of the ‘cloud01’ secret, we can now utilize it within our 01Cloud application.
Steps to use HashiCrop Vault in 01Cloud
- To begin, you must create a project and a WordPress application. Within the application, you can then click on the ‘Create Environment’ button and select a custom installation during the environment creation process. Once the ‘External Secrets’ tab is enabled, you can move forward with the setup.
- Implementing HashiCorp Vault requires specifying the server URL, secret path, version, and root token. The server URL should include the login token for the HashiCorp Vault Server. In this case, the secret path has been designated as ‘secret’ and the secret name is ‘cloud01,’ which we created previously.
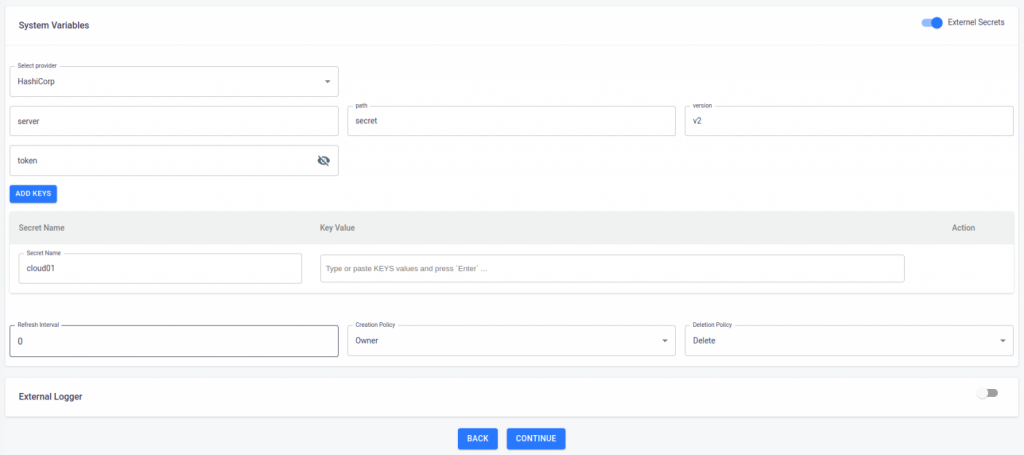
- We are now ready to move forward with the creation of the environment.
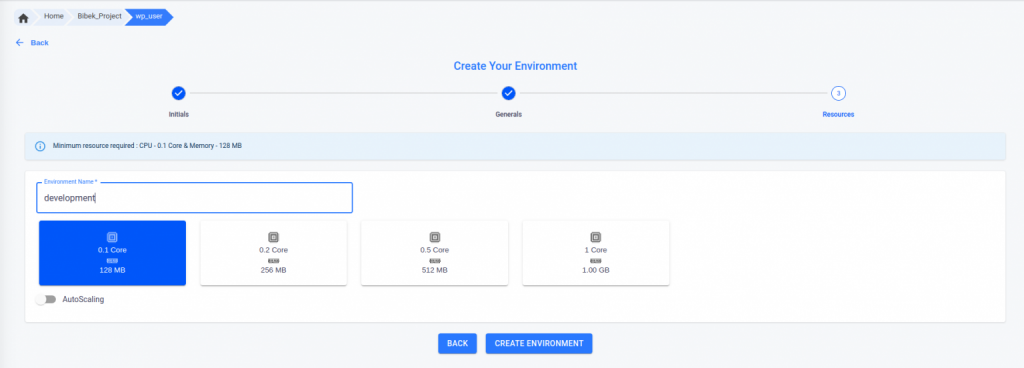
- Upon initiating the environment creation process, the authentication information provided in the external secret will be processed. If the authentication is successful, a message indicating that the secret has been fetched should appear in the activity log for the environment.
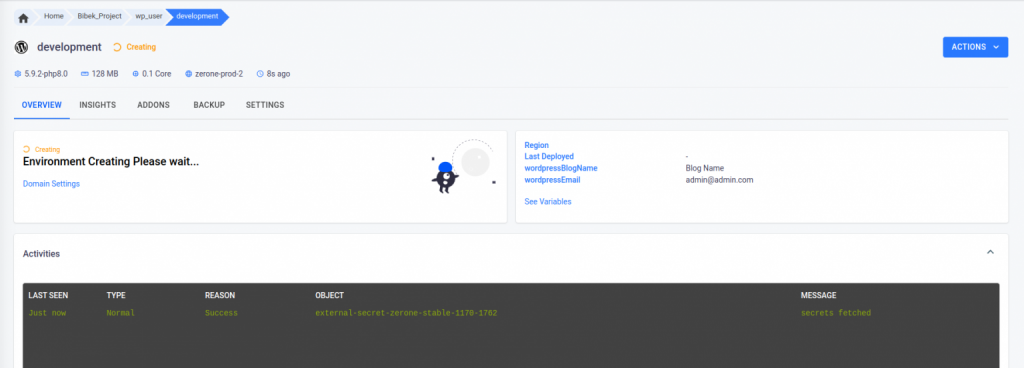
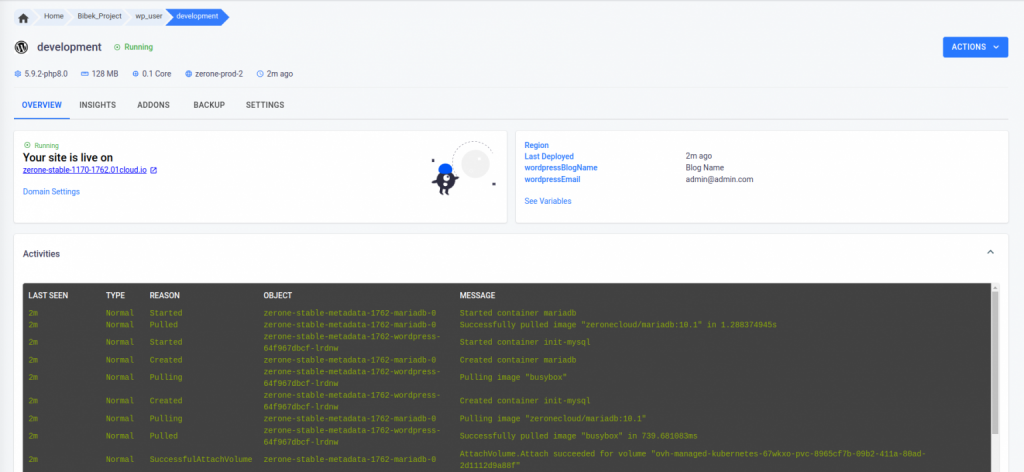
- As we can see our environment is running.
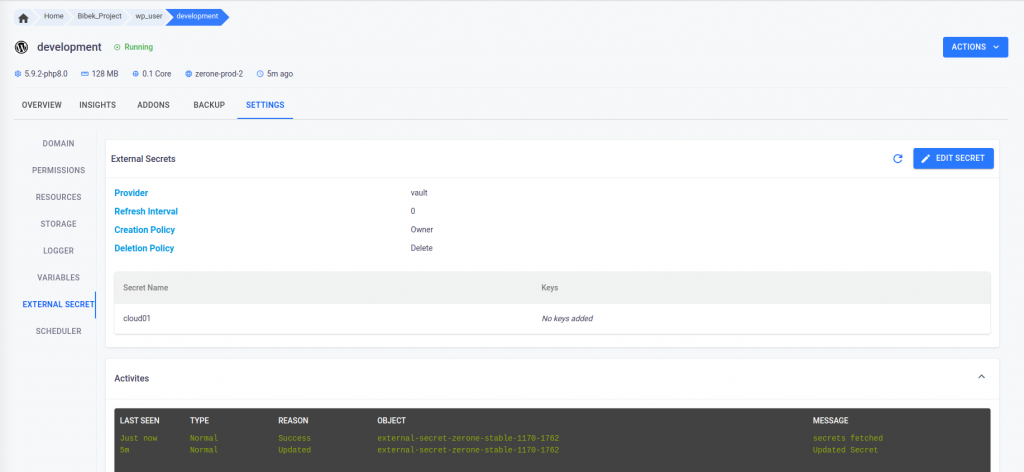
- All details regarding the external secret can be viewed in the ‘External Secret’ tab within the settings. If needed, the secret can be edited and the external secret service can be prompted to refresh the data from the external secret manager by using the ‘force-sync’ option.
Conclusion
By following these steps, you can set up and utilize the external secret feature in 01Cloud. 01Cloud retrieves the data from the external secret manager and implements it within the 01Cloud environment.