
From Vibe-Coding Chaos to Spec-Driven Precision: Why 2025’s Hottest AI Engineering Practice Is Redefining Reliable Code
As AI-assisted coding continues to reshape software development in 2025 and beyond, a clear divide has emerged between casual, improvisational approaches and more disciplined methodologies. The rise of “vibe-coding” — a term popularized by AI pioneer Andrej Karpathy in early 2025 — allowed developers (and even non-coders) to describe ideas in natural language, letting large…

Mastering Agent Development: How LangSmith Simplifies Building Reliable AI Agents
In the rapidly evolving world of AI, building autonomous agents powered by large language models (LLMs) promises immense potential—but it comes with significant challenges. Understanding how agents behave, why they make certain decisions, and how to ensure consistent quality isn’t straightforward. Non-deterministic outputs, complex tool calls, and unexpected edge cases can turn promising prototypes into…

Centralizing Helm: Why Ingress Failed and HTTPProxy Won
As organizations grow, so does the complexity of managing Kubernetes manifests. A natural evolution is moving to centralized “umbrella” Helm charts. The promise is alluring: consistency across services, reduced duplication, and a streamlined CI/CD pipeline where global policies (like security and resource limits) are enforced in one place. However, this refactor often exposes hidden architectural…
Level Up Your GPU Game: Mastering Advanced CUDA Features in 2026
NVIDIA’s CUDA platform continues to dominate GPU-accelerated computing, powering everything from AI training and inference to scientific simulations and real-time graphics. With the release of CUDA Toolkit 13.1 in late 2025, the ecosystem has seen significant advancements, including the groundbreaking CUDA Tile (cuTile Python) for higher-level tile-based programming. However, core advanced features like Unified Memory,…

Beyond Tool Chaining: Why Code Execution is the Future of AI Agents
In the year since the Model Context Protocol (MCP) launched, it has rapidly become the industry standard for connecting AI agents to the world. We’ve seen a massive shift from fragmented, custom integrations to a universal ecosystem where developers “implement once” to unlock thousands of tools. However, as agents grow more sophisticated, they are hitting…

Revolutionizing GPU Programming: NVIDIA’s CUDA Tile Lets Developers Focus on Algorithms
n the fast-evolving world of GPU computing, NVIDIA has introduced a game-changing tool that promises to simplify development while maximizing hardware efficiency. CUDA Tile, launched with CUDA 13.1, shifts the paradigm from low-level hardware tinkering to high-level algorithm design. This innovation abstracts complex GPU internals, allowing programmers to concentrate on what matters most: crafting powerful…
Open-Source Programmatic Tool Calling: LangChain Community Brings Anthropic’s Efficient Agent Pattern to Everyone
In late 2024, Anthropic introduced a groundbreaking approach to AI agent tool calling in their engineering blog: Programmatic Tool Calling (PTC) using code execution with the Model Context Protocol (MCP). This method allows agents to write and execute code in a sandbox to orchestrate tools, dramatically reducing token usage—up to 98% savings on data-intensive tasks—by…
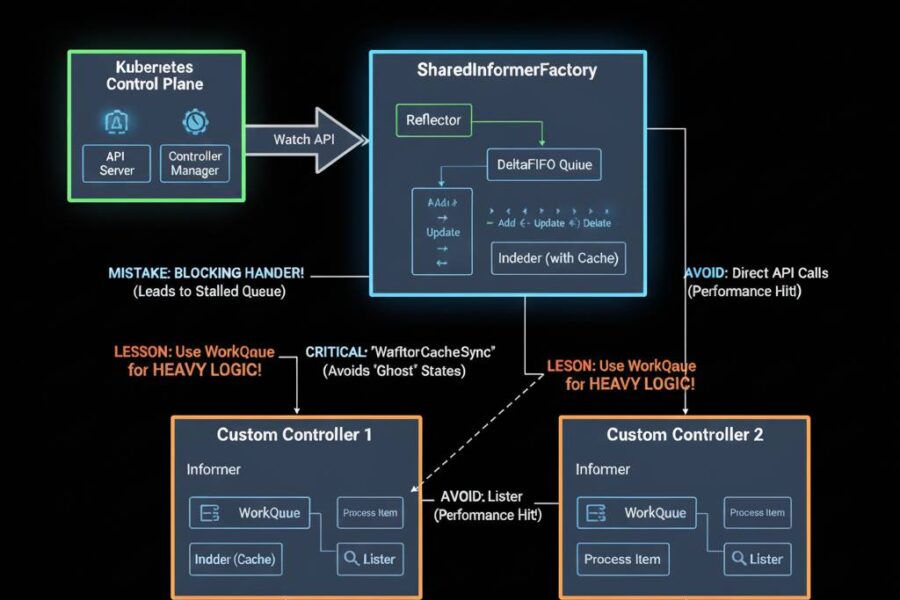
Mastering Kubernetes Informers: Lessons from the Trenches to Avoid Costly Mistakes
In the world of Kubernetes, where orchestration reigns supreme, keeping track of cluster resources efficiently is crucial for building reliable systems. At Render, engineers encountered real-world challenges while using Kubernetes Informers to monitor Pod scheduling in massive clusters. Informers, those handy tools for streaming resource updates, are incredibly powerful—but as it turns out, they’re also…
Essentials of Complex Analysis: A Computational Approach – Bringing Theory to Life with Wolfram Language
In an era where computational tools are transforming mathematics education, Wolfram Media’s latest release, Essentials of Complex Analysis: A Computational Approach by Marco Saragnese (published December 16, 2025), stands out as a fresh, interactive introduction to one of the most elegant branches of mathematics. Complex analysis, with its profound theorems like Cauchy’s integral formula and…

Avoid Breaking Your Cluster: How Kube No Trouble (kubent) Helps Detect Deprecated Kubernetes APIs
As Kubernetes continues its rapid evolution—with new minor releases every few months—cluster administrators face a recurring challenge: upgrading safely without disrupting workloads. One of the biggest risks during an upgrade is deprecated or removed APIs. If your deployments, DaemonSets, Ingresses, or other resources still reference API versions that have been phased out, the upgrade can…
