Introduction
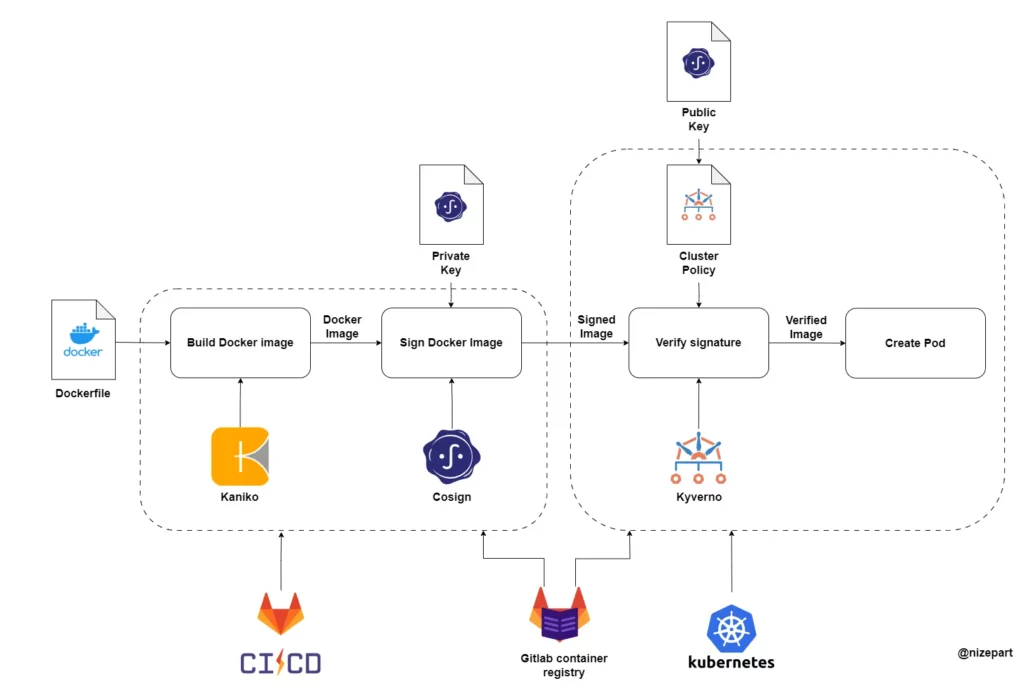
In software development, delivering quality software quickly, safely, and reliably is crucial. Docker images simplify deployment but also introduce challenges. This article, based on our work at the biotech company BIOCAD, explores automating the building, signing, and verifying of Docker images to maximize their benefits.
Building Docker Images with Kaniko
Building Docker images manually can be time-consuming and inconsistent. Kaniko, a tool developed by Google, addresses this by creating Docker images directly within Kubernetes. It doesn’t require a Docker daemon, making it ideal for environments like standard Kubernetes clusters, and enhancing security by reducing potential risks in the build environment.
Kaniko executes each command in the Dockerfile in userspace, creating a new filesystem layer for each command. This makes the build process accurate, secure, and efficient. Here’s a snippet of a GitLab CI configuration using Kaniko:
yamlCopy code.image.Build.Kaniko:
stage: "build"
image:
name: "gcr.io/kaniko-project/executor:v1.14.0-debug"
entrypoint: [""]
artifacts:
name: "digest"
when: on_success
expose_as: 'Image digest'
paths:
- digest.txt
script:
# Script to set up build arguments, Docker config, and execute Kaniko build
In your GitLab CI pipeline, you can define multiple build stages using Kaniko by extending the base configuration, allowing for flexibility and customization for different builds.
Signing Docker Images with Cosign
Ensuring the security of Docker images involves signing and verifying them to prevent tampering. Cosign, part of the Sigstore project, simplifies this process. It fits easily into existing workflows, making it ideal for CI/CD environments.
Start by creating a key pair with Cosign:
bashCopy codecosign generate-key-pair
Store these keys securely in GitLab’s environment variables or an external secrets manager. Here’s a GitLab CI job for signing and verifying images with Cosign:
yamlCopy code.image.Sign.Cosign:
image: bitnami/cosign:2.2.0-debian-11-r31
stage: sign
secrets:
COSIGN_SECRET_KEY: ...
COSIGN_PUBLIC_KEY: ...
COSIGN_PASSWORD: ...
variables:
COSIGN_YES: "true"
TARGET_IMAGE: "$CI_REGISTRY_IMAGE"
script:
# Script to generate Docker config, sign and verify image using Cosign
The job loads necessary secrets, sets environment variables, and includes commands to sign and verify the Docker image, ensuring its authenticity.
Verifying Signed Images with Kyverno
Kyverno is a Kubernetes-native policy management tool that helps enforce best practices. It can verify image signatures within Kubernetes, ensuring only properly signed images are used.
Install Kyverno on your Kubernetes cluster using Helm via Argo CD:
yamlCopy codeapiVersion: argoproj.io/v1alpha1
kind: Application
metadata:
name: kyverno
namespace: argocd
spec:
source:
chart: kyverno
repoURL: https://kyverno.github.io/kyverno/
targetRevision: 3.0.8
helm:
values: ...
destination:
namespace: kyverno
syncPolicy:
automated:
prune: true
selfHeal: true
Define a ClusterPolicy to enforce image signature verification:
yamlCopy codeapiVersion: kyverno.io/v1
kind: ClusterPolicy
metadata:
name: check-image
spec:
validationFailureAction: enforce
rules:
- name: check-image
match:
any:
- resources:
kinds:
- Pod
verifyImages:
- imageReferences:
- "registry.com/test/repo*"
attestors:
- count: 1
entries:
- keys:
publicKeys: |-
-----BEGIN PUBLIC KEY-----
YOUR_COSIGN_PUBLIC_KEY
-----END PUBLIC KEY-----
This policy ensures that only signed images from the specified registry are allowed, enhancing cluster security.
Conclusion
By automating the building, signing, and verifying of Docker images using Kaniko, Cosign, and Kyverno, we’ve created a robust pipeline that integrates security practices into our CI/CD workflows. This approach, implemented at BIOCAD, has improved our efficiency, security, and consistency, demonstrating its potential for broader application in software development environments.
Implement these tools and techniques to streamline your deployment process, ensuring a safer and more reliable software delivery pipeline.
Referece to the Article : Medium
Follw us for more Updates












